Video describing the Stealthphone information security system
Our solutions provide the security for:
- Information exchanged between users of mobile devices and personal computers via various communication channels;
- information stored on mobile devices, personal computers and external media (Flash, ZIV drives, etc.)
The concepts, forming the basis of the Stealthphone Tell and Stealthphone solutions, have significant differences in the underlying principles of design and operation, as well as functional capabilities. The main issue is the information security level which users will choose. The higher the security level, the higher the cost of the security means. The selection of the optimal security level is determined by the technical features of the means available to the enemy (e.g. hacker) which he uses to intercept information. It’s enough to use Stealthphone Tell secure network in many cases in order to preserve private information. Low cost of the software, simplicity and ease of use makes it possible for the users who’ve never used them before to quickly adapt to the operation of the Stealthphone Tell secure network.
Stealthphone information security system
"MTT" company offers its customers one of the two solutions to solve these problems:
- connect to the secure Stealthphone Tell network of "MTT" company
- create your own secure corporate network StealthPhone based on the solutions provided by MTT company.
General principles, increasing the credibility of both approaches:
- Application of cryptographic algorithms and key system parameters used in military and state information security systems
- The use of the "point to point" principle to encrypt information exchanged between users.
The use of the Stealthphone corporate network, compared to the general secure Stealthphone Tell network, provides new functionality and services, ensuring higher quality of the information security level. It is provided by the use of hardware encryption devices designed by "MTT", which comply with TEMPEST standards. With these devices users can themselves implement encryption and generate keys.
The solution the client selects is based on many factors, including:
- the possibility to independently generate and distribute encryption keys;
- the purpose of the information security systems, taking into account the purpose of their use - corporate or personal;
- required functions;
- the assessment of risks and threats to information security;
- centralized management of subscribers’ keys;
- subscribers’ network geography,
and some other factors.
Secure Stealthphone Tell network
The secure Stealthphone Tell network is an open network designed for the exchange of encrypted information (voice, image, text, data, etc.) between subscribers. It is based on public key distribution and doesn’t require prior key exchange between the subscribers. Its openness means that anyone can join the network. Secure Stealthphone Tell network operates within the Internet.
Connection to the Stealthphone Tell secure network
Anyone who has a smart phone and Internet access can connect to the secure Stealthphone Tell network and become its subscriber. It’s necessary to do the following:
- Download the Stealthphone Tell application on the smartphone from the website of MTT company;
- Pay the subscription fee for the selected period of operation in the secure Stealthphone Tell network;
- Activate the Stealthphone Tell application.
Users can start working after activating the Stealthphone Tell application, which takes just a few minutes.
What can the subscriber of the secure Stealthphone Tell network do?
The following services are available for the subscribers of the secure Stealthphone Tell network:
- Voice encryption within the secure Stealthphone Tell network;
- Sharing encrypted messages and files;
- Creation of chat groups with a possibility to send files.
A corporate Stealthphone Tell network subscriber
We offer the possibility for the subscribers to connect to the corporate Stealthphone Tell network. A group of subscribers (“a corporation”) forms its own subnet, and the services available for the subscribers of the secure Stealthphone Tell network are also available for them, but communication is possible only between the subscribers of the corporate subnet.
How does a secure Stealthphone Tell network operate?
Data Transfer in the secure Stealthphone Tell network is implemented via communication servers located in different countries and operating in the Internet. The subscriber must also have access to the Internet in order to use the services of the network.
Data encryption is performed according to the «end-to-end»principle, while such operations as encryption key generation and data encryption are performed by the subscribers themselves. Communication servers are used solely as transit nodes to exchange encrypted information between the network subscribers. Thus, network administrators cannot read the information passing through the server.
The secure Stealthphone Tell network differs from the similar solutions, offered by the competitors, by the use of digital certificates. They enable the implementation of an additional powerful mechanism (along with the mechanisms included in the ZRTP). This mechanism allows both subscribers to identity each other (mutual authentication). Public Key Infrastructure (PKI), with a Certification Center as its core, is implemented and deployed within the secure Stealthphone Tell network.
The advantages of the secure Stealthphone Tell network
The maximum security level of the Stealthphone Tell network was in the focus of attention during the development of that secure network. Along with the standard technologies we have introduced the technologies which greatly enhance the security of this solution:
- Simultaneous use of two independent (or orthogonal) approaches to security in open networks, namely the use of ZRTP protocol in conjunction with electronic certificates of subscribers’ keys;
- The use of the engineering and cryptographic analysis methods, which enhance the immunity of the Stealthphone Tell application to a number of harmful effects;
- A reinforced password security mechanism is the authorization mechanism for access to the functions and data in of the Stealthphone Tell application.
Stealthphone corporate network
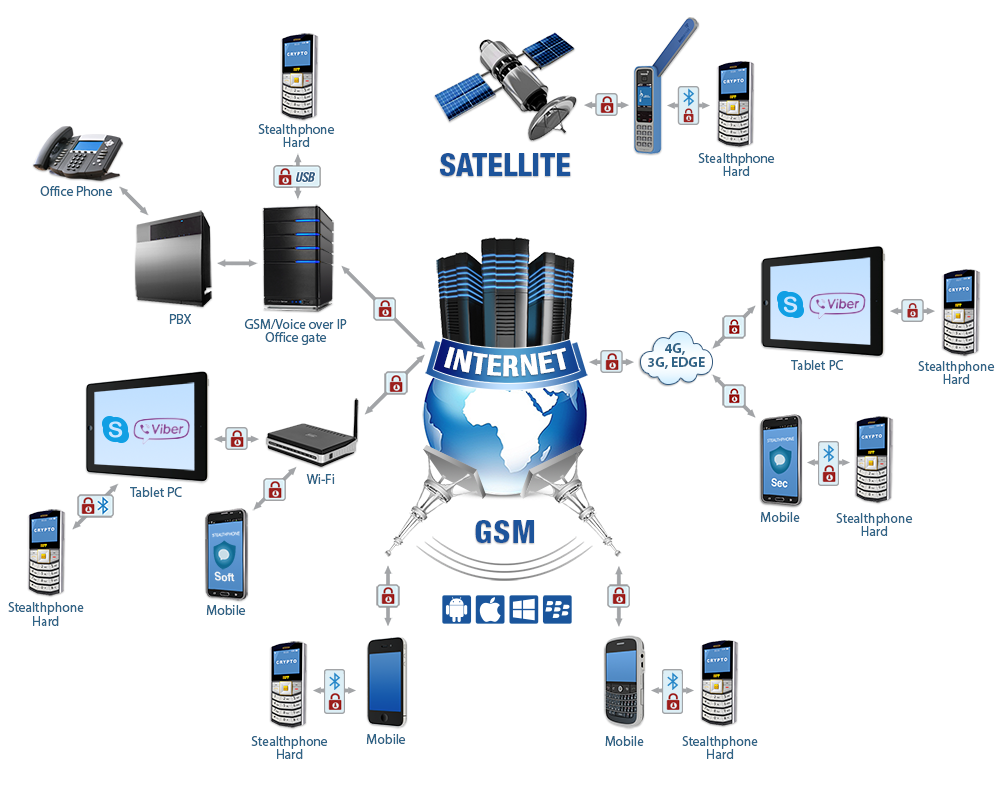
The Stealthphone corporate network safeguards information on mobile devices and personal computers. Stealthphone corporate network allows the subscribers to share encrypted information (voice, Email, text messages, files, etc.). Key management is based on the prior exchange of secret keys between the network subscribers.
Stealthphone Corporate network – multilevel defense against criminals’ attacks
We must recognize the fact that technical means which cybercriminals have at their service, are little inferior in their effectiveness to those used today by security services. Hackers’ fabulous profits play an important role: they’ve already exceeded the profits of drug lords and reached more than $ 400,000,000. Therefore, in the face of increasing multi-faceted information security threats state and private organizations are forced to use complex and multi-layered self-security measures to prevent criminal data breaches.
A bit of history
It is common knowledge that wooden doors were of superior strength in the Middle Ages. As a rule a typical wooden entrance door was made of two layers of oak boards. Wood fibers were arranged vertically in the outer layer and horizontally in the inner layer. As a result it resembled something like simplified plywood. Iron nails joined together two board layers, and the whole construction was reinforced with iron bars. The nails stuck with their spikes outward so that they could damage the weapons of the attackers who tried to break through the door.
Security features
Such multilayer protection has been in use since ancient times: even if the enemy broke through the first line of defense, he had to break through several more, suffering heavy casualties.
Stealthphone corporate network employs the same principle. Traditionally the smartphones and computers have in-built security systems. They look convenient, but are these systems really secure? Not always. The criminals try to break through this protection. That’s why we created a unique stand-alone encryption device Stealthphone Hard that secures information in mobile devices and computers. Encryption processes run separately from data transmission. Stealthphone Hard runs its own low-language OS and meets military-grade TEMPEST standard that shields against dangerous side radiation. All this secures your data against almost every kind of cyberattacks.
The network includes a number of dedicated servers that use Internet-channels. Stealthphone network has a state of the art voice encryption feature that supports various channels:
- Voice channels of mobile systems: GSM, CDMA etc;
- Voice channel of satellite system Inmarsat etc.;
- Analog phone network (PSTN);
- IP-telephony: Skype, Viber etc.
Network is managed by the administrator who is responsible for:
- Maintaining subscribers base;
- Generating and distributing encryption keys;
- Managing networks servers.
The subscribers of Stealthphone network shouldn’t necessarily work in the same organization in order to use Stealthphone network. Stealthphone network can be used by several different subscribers who entrust the administrator with the network management.
Stealthphone network includes:
- Network management system (including secret keys management subsystem);
- Communication servers system;
- Subscriber equipment – a set of software and hardware security tools
All three components are scalable; they have different features and degree of security, that’s why Stealthphone networks can be customized according to the client’s needs.
Stealthphone corporate network can be used by a small group of individuals, as well as by state organizations and major corporations.
Managing secret keys and logical structure of network
Network administrator is responsible for managing secret keys and logical structure of network.
Network administrator creates and maintains subscriber database and creates groups (overlapping and non-overlapping) of subscribers who can exchange encrypted data with each other.
Corporate network administrator generates and distributes secret pairwise keys for all the subscribers within Stealthphone corporate network. He is also responsible for scheduled and non-scheduled change of keys. He uses software uses Stealthphone key to manage secret keys and logical structure of network.
To achieve the highest quality of generated keys, Stealthphone Key software complex can be used together with hardware key generator Stealthphone Key Hard, which supports TEMPEST standard.
Communication servers in Stealthphone corporate network
Communication servers in Stealthphone corporate network use Internet channels. These servers transmit encrypted data (voice, e-mail, short messages, files etc.). The servers do not run any encryption processes, and the network administrators do not have access to unencrypted data.
The client manages servers via server management subsystem.
MTT client can design and deploy (with the help of MTT) their own system of communication servers according to their criteria (data load, network layout, geographical location and other).
Clients can also rent MTT servers.
Subscriber equipment in Stealthphone corporate network
An individual or the company (group subscriber) with internal phone network are both considered to be Stealthphone network subscribers.
To access Stealthphone network services, the subscriber must have subscriber equipment with preloaded secret keys array required for communication with other subscribers.
An individual can use application Stealthphone Soft or hardware encryption device Stealthphone Hard as subscriber equipment. A company must use software-hardware complex Office Gate.
Stealthphone Soft is an application which is compatible with most mobile OS (Android, Windows Phone, iOS, BB). Stealthphone Soft meets all the standards of engineering cryptography. The application is easy to install and user-friendly. Stealthphone Soft allows the users to exchange encrypted data (voice, e-mail, short messages, files etc.) via communication servers of Stealthphone network. Internet connection is required to access network services.
Stealthphone Hard is a unique hardware encryption device designed to meet the highest requirements (including TEMPEST standard) for data security equipment. Hardware encryption device allows the users to encrypt data, generate and store keys. Data transmission is carried out by the mobile device or PC connected to Stealthphone Hard.
Stealthphone Hard is compatible with almost all mobile devices and computers; it is connected to them via Bluetooth or USB.
Hardware encryption device Stealthphone Hard works in several modes:
- Communication servers mode. In this mode the subscriber has access to all the features available in Stealthphone Soft (encryption of voice, e-mail, short messages and files). The encryption device is connected to the PC with preloaded application Stealthphone Sec that performs interface and communication functions, but all the encryption processes are run by Stealthphone Hard. In this mode Stealthphone Hard and Stealthphone Soft are fully compatible; Internet connection is required to exchange data.
- Voice encryption mode (via external communication channels in mobile networks, satellite communication channels, analog phone lines, IP-telephony applications). In this mode Stealthphone Hard is connected to the device (mobile phone, satphone, landline, smartphone or PC with preinstalled IP-telephony application) as a standard headset. Stealthphone Hard encrypts traffic exchanged between subscribers who both use Stealthphone Hard.
- PC data encryption mode. In this mode Stealthphone Hard is connected to the computer (Windows или Mac OS) via USB. This mode allows to encrypt logical disks or separate files and to exchange already encrypted files with the subscribers via any e-mail service (Gmail, MSN, Yahoo, …) or social networks(Facebook, Twitter, …).
OfficeGate is a crypto gateway connecting subscribers of Stealthphone corporate networks with office phone network. OfficeGate secures phone connections between subscribers of Stealthphone network and office employees. The voice traffic is encrypted during its transmission between crypto gateway OfficeGate and the subscriber (or between two OfficeGate). Voice traffic is transmitted in open form within the network. OfficeGate allows the subscribers to make out-of-network calls by connecting with OfficeGate, decrypting voice and redirecting the call via office phone network.
List of products for information security
For individuals
|
Stealthphone information security system for corporate clients and goverment organizations
|
||||
| Stealthphone Tell
|
|
|
|
|
|
|
|
|
|
|
|
|
The main advantages of the information security system Stealthphone
- A hardware encryption device Stealthphone Hard designed to encrypt voice (VoIP), SMS and data in smartphones, tablets and PCs guarantees the highest security level according to TEMPEST and military grade encryption
- First ever strong encryption of voice over GSM channel (VoGSM)
- Strong voice encryption for Skype, Viber and other IP-telephony applications
- Secure calls between the corporate phone network and the Stealthphone network
- Cryptomessenger is used to exchange instant messages, all types of files and multimedia information
- E-mail client is used to exchange encrypted e-mail, all types of files and multimedia information
- Full control over encryption keys
- Key generation using the hardware random number generator Stealthphone Key Hard
- Flexibility, scalability and adaptability of the system. The possibility to develop solutions, from low-cost solutions to the solutions for big private companies and state agencies
Our presentation
The encryption algorithm is a strong 256 bit symmetric encryption algorithm Tiger, a proprietary MTT design.
Tiger is a synchronous additive stream cipher. Synchronization is provided by an initialization vector, transmitted (or stored) in an open form together with the ciphertext. The length of the initialization vector ranges from 4 to 12 bytes, depending on the scenario used.
The encryption device should first be initialized to enable it. The initialization procedure requires a secret key and an initialization vector to commence. The initialization outputs the values of all status elements of the encryption device.
Learn more about our Encryption Algorithms
Learn more about our Symmetric Encryption Algorithms
Learn more about our Asymmetric Encryption Algorithms
Learn more about Hardware Encryption System for E-Commerce and Mobile Banking Security
Maintaining data integrity
Algorithms, providing the data integrity test, are needed to protect data (stored in the encryption device, a smartphone or a PC or encrypted data exchanged by the subscribers) against accidental or intentional distortion.
Data authentication is executed by computation of the one-way function, data and the secret key should be input to the function. The calculation result of the one-way function, also called “data authentication code” (or “message authentication code”) is stored or transmitted together with the data. Any data alteration causes the alteration of the authentication code. It is impossible to match it without the secret key, even if the one-way function properties are selected correctly.
HMAC-SHA256 algorithm is used in Stealthphone and StealthTell systems as a basic algorithm for computing of a data authentication code.
The data authentication code is computed and checked in all the solutions for all types of encrypted data: voice, SMS, instant messages, E-mails and all types of files and multimedia information transmitted or stored in the protected memory of the encryption device, a smartphone, a PC or an SD-card.
All encrypted data undergoes an integrity check.
Learn more about Authentication, Integrity And Non-Repudiation
Computations in the cluster of points of the elliptic curve to authenticate the subscribers and negotiate session keys
Asymmetric cryptographic elliptic curve-based algorithms (ECC) are used in common key agreement protocols to encrypt voice in Stealthphone and StealthTell systems and also in subscriber authentication protocols of the StealthTell system.
The cryptographic security of the elliptic curve-based systems, is founded on the Elliptic Curve Discrete Logarithm Problem (ECDLP).
The complexity of the best currently used ECDLP algorithms is exponential, whereas the running time of such tasks as the factoring whole numbers and logarithmation in finite fields (they are the basis of the alternative algorithms RSA and El-Gamal) is sub-exponential.
It means that the required security level in elliptic curve systems is achieved with shorter key length, compared to the RSA system for example. For comparison, a 384-bit ECC key provides the same security level as a 7680-bit RSA key. The shorter key length in EEC, compared to the alternative variants, allows accomplishing high-tech solutions. In fact, while the crypto security level is the same, it is possible to achieve the substantial increase of the computation speed and reduce the volume of transmitted data.
The National Security Agency of the USA has approved the use of asymmetric cryptographic algorithms based on elliptic curves (with 384 bit key length) to process top secret documents.
384-bit elliptic curves are also used in Stealthphone and StealthTell systems. The cryptographic security of the cryptosystems based on ECC is based not only on the elliptic curve length, but also on the mathematical parameters of the elliptic curve cluster points, where computations are performed.
The parameters of a group of the elliptic curve cluster points, where the computation is accomplished in Stealthphone and StealthTell systems, entirely provide the required cryptographic characteristics.
Cryptographic algorithms for Voice over GSM Encryption
Strong time-frequency transformation of voice is used to protect voice transmitted over GSM channels. This transformation is resistant to double vocoder transformation.
The main transformation elements are:
- Splitting a voice signal into linear elements
- Non-linear transformation of linear elements
- Interchange of voice elements
- Processing of the incoming signal to transmit over the AMR voice codec and a GSM channel
The transformation parameters (the number and the length of voice signal elements) depend on the key.
Non-linear parameters are also defined by the cryptographic key.
The total algorithmic and system delay (caused by the cellular network) does not exceed 2.5 seconds.
Download this PDF to learn more about strength of cryptographic transformations.
Voice encryption algorithms for IP telephony software
When IP telephony applications are utilized, including Skype and Viber, guaranteed security time-frequency transformation of the voice signal provides the protection of voice information and converts the speech into a noise-like signal.
The transformation consists of:
- N-filter comb (a filter bank)
- Dispersive delay line (a filter with random phase-frequency characteristics)
- N length substitution
The transformation properties (the number of filters, the delay line parameters) depend on the key.
The repositioning of the spectral bands in a filter comb is set by the session key once the connection is established.
The bands are rearranged once every 3-5 seconds to execute a dynamic transformation.
The algorithmic time delay does not exceed 1 second. The band of the processed voice signal is 300-3400 hz. The minimum length of N substitution is 24.
There may be several transformations depending on the traffic capacity of Internet connection. The permitted extreme delay is 2 seconds. If Internet connection is slow or unstable, an algorithm, that does not require synchronization, may be used. It provides quick handshaking and stable cryptographic connection.
The potential vulnerability of the static transformation is balanced out by the forceful limitation of the connection time and reconnection using new session keys.
Key management
When it comes to the creation of cryptographic information security systems, keys management is one of the most challenging tasks of the applied cryptography. According to our estimations, the vulnerabilities in some elements of the key management system (generation, storage, usage, distribution and protocol exchange protocols) are the principal causes of ISS compromise.
That is why the key management lifecycle is the subject of particular attention in Stealthphone and StealthTell systems – from key generation to key deletion or key change.
The most important key management issues are described below.
Key Quality Control
When keys are generated by software (Stealthphone Hard, Stealthphone Key Hard) or hardware means (Stealthphone Soft, StealthTell, Stealthphone Key) the key quality is constantly controlled to check their statistic parameters and detect the presence of patterns.
Hardware generators use random number generators based on physical processes. Their characteristics have been scientifically confirmed by special laboratory testing.
Software generators are designed according to the constant entropy accumulation principle – an actual random sequence – and its further use to generate encryption keys.
Various events in a smartphone, a tablet or a PC may be the entropy source.
Character input when the text is entered is an example of the event. If the key generation system considers the volume of the initial entropy to be insufficient, a user may be advised to perform some manipulations with the device to complete it.
The entropy accumulation procedures executed in software key generators have been thoroughly tested and confirmed their excellent characteristics.
In all types of key generation the generated keys undergo various procedures to execute the dynamic control of their statistic characteristics.
Key storage
All keys (including those stored in Stealthphone Hard encryption device) are stored in the encrypted form or are not stored anywhere. They are generated “on the fly” from a password and some additional data.
The decryption of encrypted keys is performed only when they are used for encryption. They are in the decrypted form while the operation is in process. They may also be masked and securely stored in the device memory.
Key Classification
Though there are differences of principle between the architecture of Stealthphone and StealthTell key systems, they are based on the common key classification principles, clearly governing key usage rules:
- All keys are subdivided into two types – data encryption keys and key encryption keys. It means that each encryption key is used either to encrypt data (including voice) or exclusively to encrypt keys, in particular those, which are used to encrypt data and voice
- All keys are subdivided into long-term keys and one-time keys. Long-term keys are repeatedly used within a certain period of time; one-time keys are used only once to encrypt a data fragment or a voice fragment. Long-term keys include all key encryption keys, and also data encryption keys in a smartphone or a PC. Scheduled and unscheduled substitution procedures are set forth for long-term keys, in case they are lost or compromised
- All encryption keys may be arranged in an certain hierarchy:
- There is an authentication key at the very top of it. It is not stored anywhere and is generated as a result of the subscriber authentication by the device according to the password
- Next there is a master-key, encrypted with the help of the authentication key. The master-key is used to encrypt:
- all key encryption keys used to encrypt data
- all data encryption keys stored in a Stealthphone Hard, a smartphone, a tablet or a PC.
- The next level includes key encryption keys, used to encrypt data. These keys are encrypted by the master key and are used to encrypt one-time data encryption keys and keys used to generate session keys for voice encryption.
- The lower level is presented by the keys, used to encrypt data. Each data encryption key is encrypted
- Only one-time session encryption keys are used to encrypt voice. They are deleted at the end of the conversation. The volume of voice data, encrypted with the help of a one-time session key, is limited
- Only one-time keys are used to encrypt transmitted data; the volume of data, encrypted with the help of a one-time key, is limited
Specific Features of Stealthphone Key System
The secure exchange of encrypted data in the Stealthphone system is possible only within one cryptographic network (Stealthphone network). The subscribers of the network can exchange the following four types of encrypted data:
- Voice data (voice encryption)
- SMS messages
- E-mail messages
- Text messages and files (messenger)
A session key is used to encrypt voice. A session keys is generated by combination of the key, generated with the help of ECDH method, and a pairing connection secret key, used to encrypt voice and shared by two subscribers.
The other three types of data – SMS messages, E-mail messages and text messages - are encrypted by one-time keys, randomly and equiprobably generated at the transmitting side. In order for the receiving side to decrypt the data, the one-time key and the data are encrypted by Tiger asymmetric algorithm and sent together with the encrypted data. The one-time keys are encrypted with the secret pairwise key, belonging to both subscribers.
Therefore, each pair of subscribers within one crypto network shares a set of four different pair communication keys, each set serving one type of data encryption.
A pairwise voice encryption key is utilized in the procedure to generate a session key to encrypt voice.
A pairwise SMS key is used to encrypt one-time keys, used to encrypt SMS messages.
Pairwise Email and messenger keys are used the same way as a one-time pair-wise SMS key to encrypt e-mails and files sent over the messenger.
The total number of pairwise keys for each subscriber, used to exchange encrypted information with the other network subscribers, is 4 × (N – 1), where N is a number of network subscribers.
Pairwise voice encryption keys of all Stealthphone network subscribers can be arranged in one N × N square table (matrix) according to the following rule:
- Matrix diagonal is unfilled (contains zero elements)
- There is a secret pairwise key, used to encrypt voice data of subscribers A and B, at the intersection of line A and column B
The same approach can be used to create pairwise key matrices for the other types of data. All four matrices are symmetric about the diagonal.
If we combine four matrices we’ll get a full pairwise key matrix, symmetric about the diagonal, of the Stealthphone network. It will contain all the pairwise keys, which each pair of Stealthphone network subscribers will require to securely exchange all types of data. At the intersection of line A and column B there is a full set of 4 secret pairwise keys for the subscribers with cryptonumbers A and B.
Number A matrix line forms a set of all pairwise keys required for the exchange of encrypted data between the subscriber with cryptonumber A and the other network subscribers. The total number of keys in the line is equal to 4 × (N – 1).
The pairwise key matrix of the Stealthphone network and all the other subscribers’ keys are generated by the network administrator with the help of a StealthKey complex. StealthKey complex is used to download keys into subscribers’ devices at the administrator’s work station. A subscriber can also upload the keys himself, using a PC and the key set, prepared in advance by the administrator.
In order to maintain the maximum security level and to streamline the key management in the Stealthphone network, it provides the possibility of the initial one-time key uploading into subscribers’ devices. There is no need to reupload the keys, if the network structure changes (subscribers’ access rights are terminated/added/changed), or in case the keys of the other subscribers are compromised, or there’s a scheduled change of all keys of the network subscribers.
Thus the initial key uploading into subscribers’ devices may be enough for a few years and there will be no need to reload the keys.
Methods for Protection against Dangerous Electromagnetic Emissions (TEMPEST Standard)
The problem of studying linear and other electric circuits of the cryptographic equipment is called forth by available principle possibility to restore keys or non-ciphered (clear) information as a result of intercept of its microtrace generated at the time of processing the above mentioned information in the components of the equipment. The subject of special examination also includes electromagnetic fields, channel circuits and outcoming wiring of the equipment in which researchers can find trace of key and clear information caused by the functioning of the internal components of the cryptographic equipment.
For example, let's consider the output signal of the electronic cryptographic equipment – sequence of pulses representing abstract zeros and ones. In any electronic equipment such pulses are to comply with some standards so that they can be identified by the other parts of the system. In cryptography there are some additional requirements: pulses representing identical values must be identical as much as possible.
Cryptographic equipment, like any other devices, is typical of electromagnetic emission caused by short pulses use. As any emission of a cryptographic device can be intercepted by adversaries and analyzed for obtaining useful information, there must be provided a protection against such attack, for example, by way of shielding units and blocks of the equipment. The first stage of shielding is intended to divide strictly the device into "red" (restricted) zone within which there is a plain text, and "black" (unrestricted) zone, within which there is only a ciphertext. The device must be designed so that all traffic lines between "red" and "black" zones be protected to provide passage of only designated information via them.
The adversary can organize an active attack, directing emission of high energy at a communication terminal and monitoring the reaction, expecting to obtain any information on its internal state.
The general attitude to estimating an extent of cryptographic equipment protection consists in selecting (on the basis of the analysis of proposed circuit designs) sources of dangerous signals, discovering, by experimental methods, among them the most informative ones and measuring the levels of dangerous signals from the selected sources through the leakage paths. Then a degree of informativeness is determined by calculating the signal-to-noise ratio at the output of the receiver under the conditions of operating masking noise and comparing the obtained data with the accepted values.
Steganography
The principle of steganographic methods of information protection is that a violator cannot distinguish meaningful information in the stream of data circulating in the system. Therefore, in this case no issue on possible access to protected information exists at all, because
it is absolutely unclear what data should be distinguish as meaningful. It is generally agreed that the basic requirements for steganographic systems are as
follows:
- steganographic methods must ensure authenticity and integrity of files;
- an enemy possesses complete knowledge of steganographic methods;
- steganographic methods must retain principal properties of a file transmitted in clear mode (a stegocontainer) when a confidential message and certain service data unknown to the enemy, for example a key, are entered into such file
- if an enemy knows about transmission of a certain hidden message, an extraction of the confidential message out of the stegocontainer must represent a complex computational problem.
There are several ways the steganography can be used. They differ principally by the type of containers – those files or messages in which confidential information is built. Graphic and sound containers are traditionally used. Their inherent redundancy allows an additional informational component to be included without detection of its masking container. Considering the fact that current information and telecommunication technologies are digital, the most
effective approach seems to be the one that uses the least significant bits of digitized images or acoustic signals as components carrying useful information.
